What is End-to-End Encryption?
End-to-end encryption (E2EE) means your data is encrypted on your device (eg, a text message or a file), and only the intended recipient can decrypt it, or open it. No one in between this chain - not service providers, not hackers, not governments – only you, and the reader.
The global privacy-enhancing technologies market reached between $3.12 billion and $4.40 billion in 2024, projected to grow to $12.09-28.4 billion by 2030-2034. Cryptographic techniques including end-to-end encryption, control 54% of market share. This growth reflects increasing demand for genuine data protection in a world where our data is no longer ours. Think of it like this...
The Lock and Key Analogy
- E2EE is like sending a locked safe through the mail:
- You create a message (put valuables in the safe)
- You lock it with a key only your recipient has (encrypt on your device)
- The postal service carries the safe (data travels through servers)
- They can't open it – they only transport it
- Your recipient unlocks it (decrypts with their key)
- Only they see the contents
The critical point: The delivery service (the company running the app) never has the key. They transport encrypted data that's meaningless without decryption.
How End-to-End Encryption Works Technically
Step 1: Key generation
When you create an account, your device generates a unique encryption key pair – one public, one private. The private key never leaves your device.
Step 2: Encryption
When you create a message, task, or file, your device encrypts it using the recipient's public key. The encrypted data (ciphertext) is unreadable scrambled information.
Step 3: Transmission
The encrypted data travels to the server. The server stores and routes it, but sees only ciphertext – meaningless without the private key.
Step 4: Decryption
The recipient's device receives the encrypted data and decrypts it using their private key. Only then is the content readable.
The fundamental principle: Private keys exist only on user devices. The server never sees unencrypted content or decryption keys.
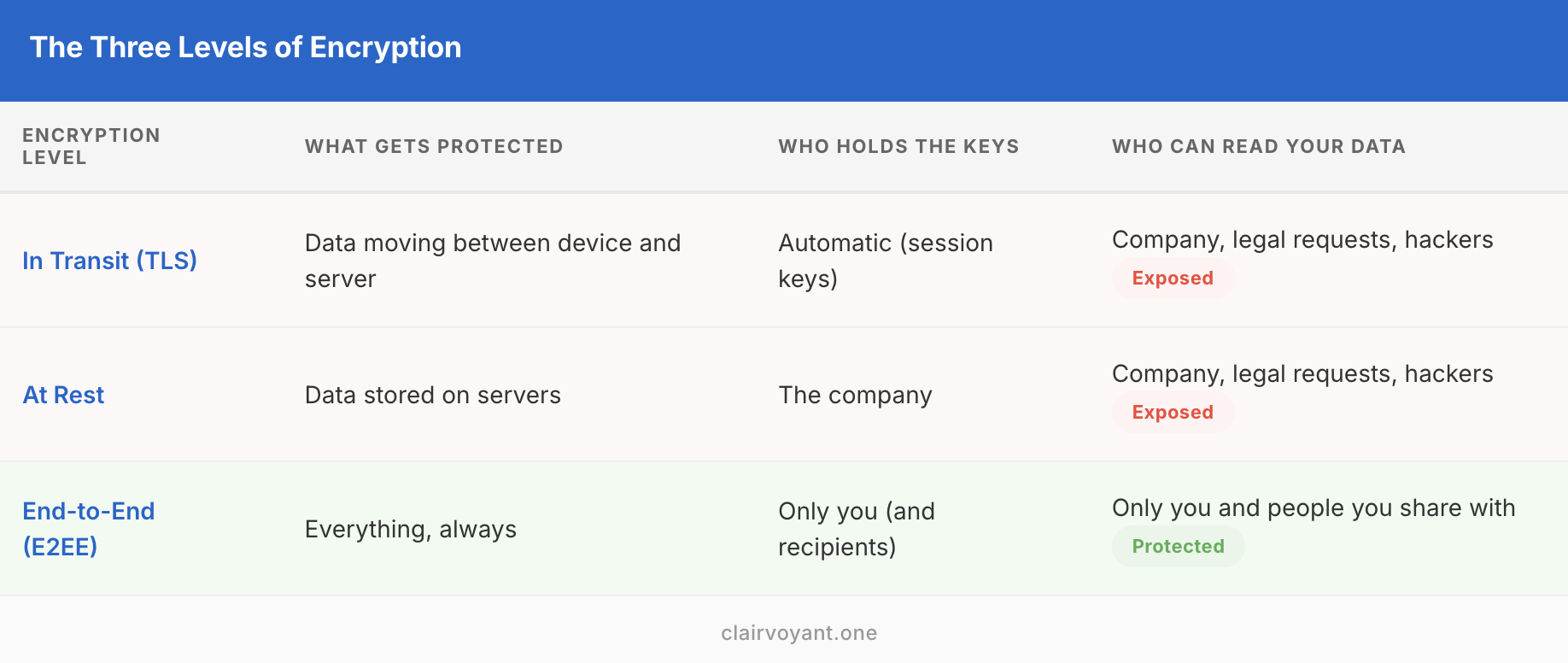
The Three Levels of Encryption
Most services offer the first two levels and call themselves "encrypted." Which is _technically _true. 87% of companies plan to increase encryption investments in 2026, but "encryption investment" often means at-rest encryption – not E2EE.
The Key Question: Who Holds the Keys?
If a company can reset your password and restore all your data, they hold the encryption keys.
With true E2EE and zero-knowledge architecture, you control the encryption keys. This means:
- The company cannot recover your data if you lose your passwords (make sure you save them using tools like ProtonPass to make your life easier!)
- Employees with server access can only see encrypted gibberish like a cat's jumped on your keypad
- A data breach exposes encrypted data that's useless without keys
- Legal requests for readable data cannot be fulfilled – the company lacks the decryption capability
Over 50% of organizations have implemented cryptographic programs, and 71% have adopted formal policies with well-defined encryption standards. Yet only 25% fully apply encryption and access controls across transit, storage, AND processing.
What E2EE Protects Against Data Breaches
The average cost of a breach in the United States reached $10.22 million in 2026. When hackers breach a service with E2EE, they get encrypted data. Without the keys, it's useless.
Recovery extends beyond 100 days for most organizations, with only 12% achieving full recovery. This is where E2EE is amazing for businesses and personal use, as it dramatically reduces breach impact.
Insider Threats
With E2EE, company employees cannot read your content – even with full server access. There's no "admin mode" that decrypts everything.
Legal and Surveillance Requests
If authorities demand user data, a company with E2EE can only provide encrypted content. They literally cannot comply with requests for readable data because they lack decryption capability.
Man-in-the-Middle Attacks
Even if someone intercepts data in transit, it's encrypted with keys they don't possess.
What E2EE Does NOT Protect Against
E2EE is powerful but not complete protection:
- **Device compromise: **If malware infects your device, attackers can see data after you decrypt it. E2EE protects data in transit and storage, not on a compromised endpoint.
- Screenshots and forwarding: Once you view decrypted content, you can share it through other means. E2EE can't prevent human-initiated sharing.
- Metadata (sometimes): E2EE protects content but not always who you communicate with, when, and how often. Some services also encrypt metadata; many don't.
- Weak passwords and authentication: If someone guesses your password, they access your account normally. Use strong, unique passwords with two-factor authentication.
- Social engineering: If you're tricked into sharing access credentials, encryption can't help. Security includes human factors.
How to Identify Genuine E2EE
Before trusting "end-to-end encrypted" marketing claims, verify these points:
- Customer support access test: Can support staff view your content to troubleshoot? If yes, it's not E2EE.
- **Password recovery test: **Can they reset your password and restore all your data? If yes, they hold the keys.
- **Documentation test: **Is the encryption protocol publicly documented? Legitimate E2EE services publish technical specifications.
- **Audit test: **Are there independent third-party security audits? Look for published audit results from reputable security firms.
- **Key storage test: **Where are encryption keys stored? Keys should exist only on user devices, never on company servers.
Red flags to watch:
- "Encrypted" without specifying the type
- Password reset that recovers all data intact
- "We take security seriously" without technical specifics
- No published security documentation or audits
- Closed-source proprietary encryption
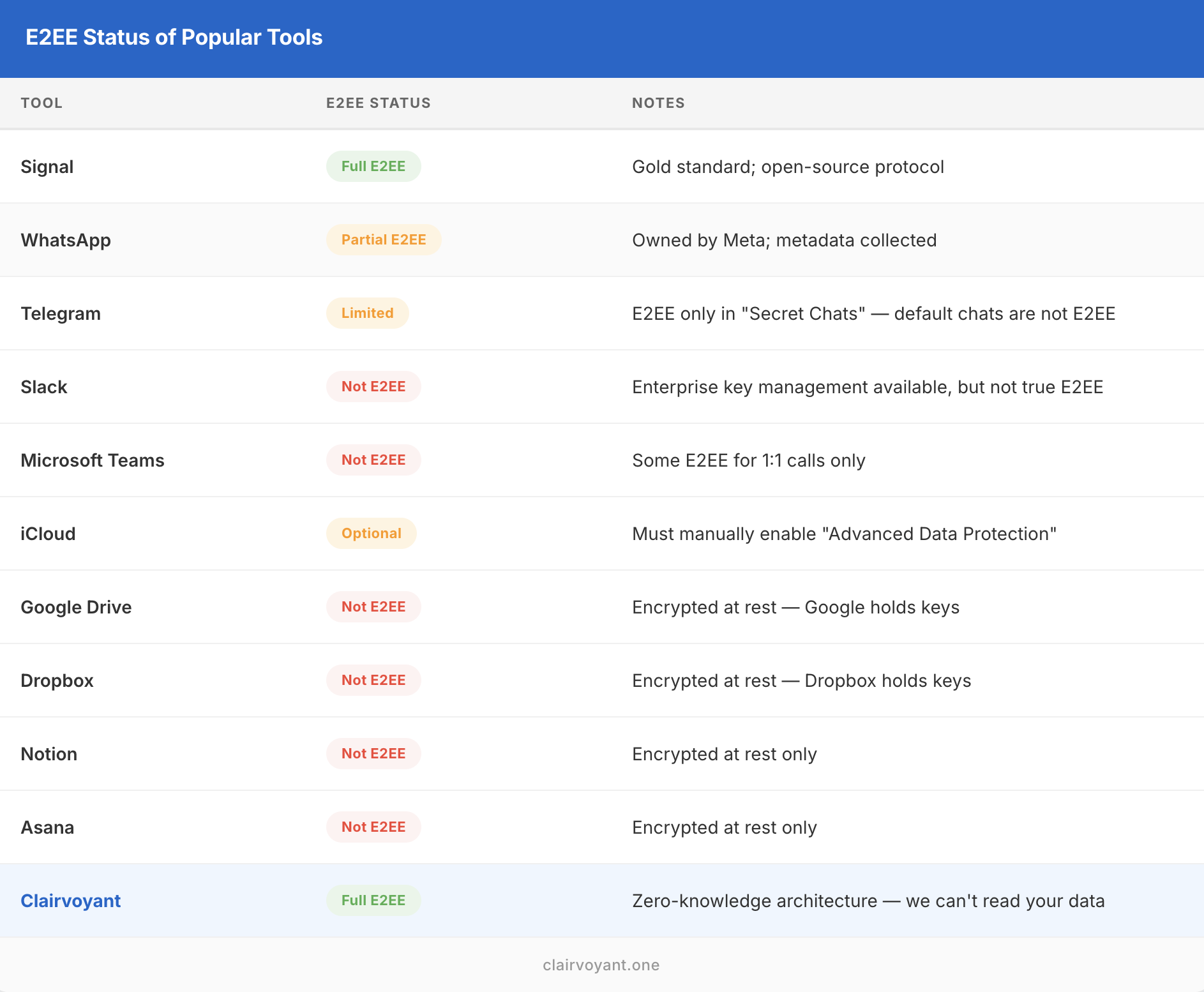
E2EE Status of popular Tools
For most users handling sensitive information, these tradeoffs are worth the protection, but understand the limitations before adopting!
Frequently Asked Questions
Is end-to-end encryption legal?
E2EE is legal in most countries. Some governments have proposed mandatory "backdoors" for law enforcement access. However, security experts universally agree: there's no such thing as a backdoor only good actors can use. A backdoor for law enforcement is a backdoor for attackers.
Does E2EE slow things down?
Modern encryption is computationally efficient. You won't notice performance differences in daily use. The encryption and decryption happen in milliseconds on modern devices.
If E2EE is better, why doesn't everyone use it?
E2EE limits what companies can do with your data. They can't analyze it for advertising, train AI models on it, or easily comply with data requests. For ad-supported services, E2EE conflicts with the business model. For productivity tools, it makes certain features (AI assistants, advanced search) more difficult to implement.
Can I add E2EE to tools that don't have it?
For files, you can encrypt before uploading using tools like Cryptomator. For messages, tasks, and notes, the tool itself must implement E2EE at the application level. You can't retrofit E2EE onto existing services.
What's zero-knowledge architecture?
Zero-knowledge means the service provider has zero knowledge of your data content. It's the implementation of E2EE where even the company cannot access user data – by design, not policy.